Policies¶
Ericom Shield allows an organization to define different policies that best protect the business from external threats while still allowing the business to function. In today’s world, almost every employee needs access to the internet to complete their work. Ericom Shield offers a level of protection out of the box, but it’s possible to go further and define additional policies that provide additional protection. For example, instead of allowing full access to the internet, internet access can be blocked apart from a list of whitelisted sites. Or full access can be granted to all sites, but only downloads from whitelisted sites is allowed. This level of granularity can be achieved by defining policies as described in this section.
Intelligent Isolation Mode¶
Shield includes an embedded URL filtering mechanism, where Categories policies are defined in the system and can be assigned values as desired. When evaluating Shield, it comes by default operating in Intelligent Mode, where uncategorized and suspected categories (as defined by the URL filtering mechanism) are Shielded. All other categories are set to white. Some actions are available only in Full Isolation Mode license (e.g. set a category to be Shield or delete/add categories).
Categories policies can be defined in Shield and assigned with different policies options. The use of this filtering mechanism requires a license add-on. All that is described hereunder is relevant only with the relevant license add-on.
Notifications may appear at the top of the table, with details about current license and mode of operation (Full/Intelligent Isolation). Please follow the information in these notifications to enjoy the filtering functionality to the fullest.
Some options may be enabled/disabled per the specific acquired license.
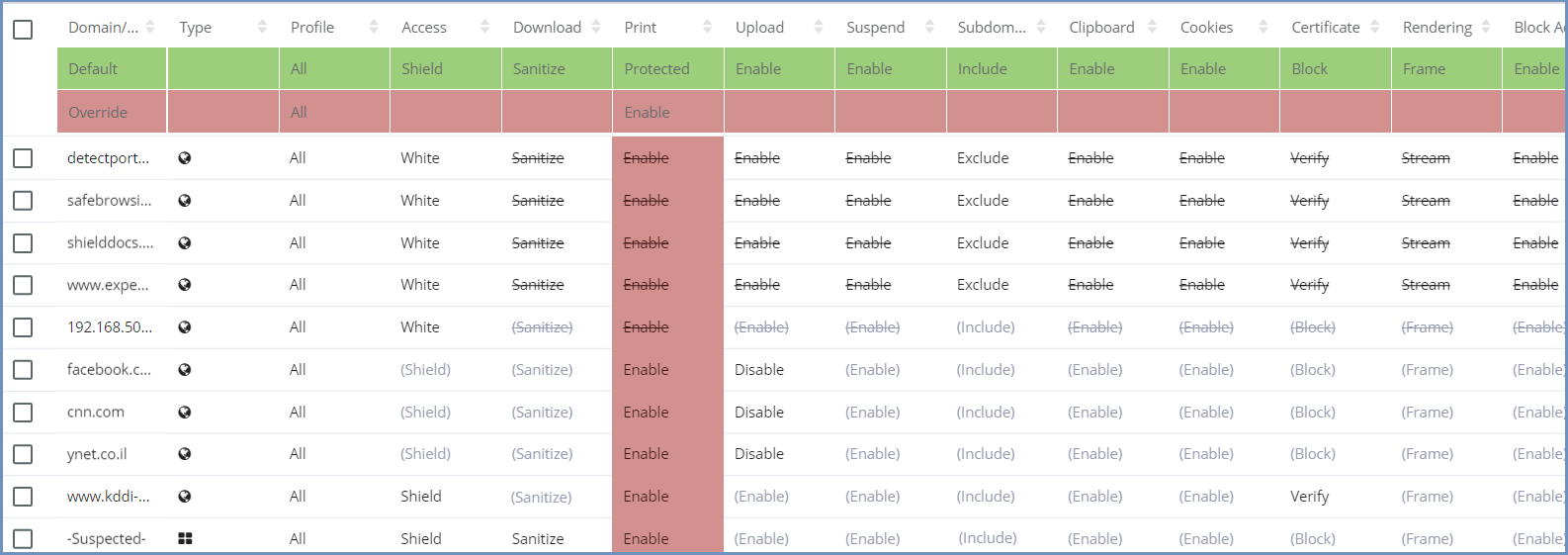
Policies Table¶
Policies can be defined per specific domains, IP addresses or categories. In addition, there are System Defaults policies and Override policies which affect the entire system. The system comes with predefined defaults for each policy. These can be easily changed from the dedicated entry. As for the Override - this is a highly useful tool that enables the administrator full control system-wide. For further information on the System Default and the Override policies, see below.
Policies can be defined per a specific Profile or per the default All profile.
The Policies table includes a list of domains, IP addresses and Categories, with their defined policies.
If the categories are disabled (via the matching setting in the Settings section), a notification will be issued, and the table will include only domains/IP addresses.
To identify if a certain entry represents a domain/IP address or a category, use the Type icon
In the upper bar there is a profile filter and the available actions:
Add New Domain, Add New Category, Delete, Export Policies and Import Policies. In addition, there is a search box, which allows to search for a specific domain/IP address or category.
Available Policies¶
The following policies are available within Shield, either at the System Defaults level or for specific domain:
Access – define whether the domain is:
- Shield - opened via Ericom Shield
- White - opened without going through the Ericom Shield system
- Black - completely blocked
Download – define if a file may be downloaded and sanitized from the specified domain. The possible values are:
- Enable - the file is downloaded (without sanitization)
- Sanitize - the file is sanitized and if sanitization was successful, file is downloaded
- Preview - the file can only be previewed (in a dedicated pdf viewer) but cannot be downloaded
- Disable - file cannot be downloaded, sanitized or previewed
Note
Download policy affects the Print policy.
Print - define if a file may be printed. When printing a file, it is downloaded first and then printed, therefore the Download policy affects the Print policy. The possible values are:
- Enable - printing is always possible, regardless of the Download policy
- Protected - printing is allowed only if download is allowed (either Enable/Sanitize). If Download is not allowed then printing is disabled as well
- Disable - printing is completely disabled
Upload - define if a file may be uploaded to the specific domain. Possible values: Enable/Disable
Suspend - define if the domain, while in idle state, will be suspended (according to a certain timeout) or remain active. The possible values are:
- Enable - domain will be suspended, when idle, until R/O & R/W timeouts are met (for more details see Resources section)
- 3 available timeouts - 1h/4h/8h
- Disable - domain will remain active until Terminate timeouts are met (for more details see Resources section)
Sub-domain – define whether the domain’s sub-domains are included or not. E.g., if example.com is defined as a domain and sub-domains = include, then both west.example.com and east.example.com are included and affected by all policies values defined for example.com. There’s no need to explicitly add them to the domain section.
Note
when sub-domains = exclude, only the exact specific domain will be matched. E.g. if example.com is defined as a domain and sub-domains = exclude, then www.example.com will not be matched by the policy.
- Clipboard – enable or disable the clipboard usage
Note
Clipboard policy affect both texts AND images. Disabling the clipboard will prevent copying and pasting of texts AND images to and from the remote browser. In this case these options are available internally (within the remote browser only).
- Cookies – enable or disable the usage of cookies (bi-directionally)
Note
Since most sites use some form of authentication using cookies, globally blocking cookies will make these sites unusable. However, the main reason to block cookies is to prevent tracking cookies, leading to malvertizing and retargeting (receiving annoying ads based on past searches etc.). As blocking all cookies may cause issues with some sites needed by the organization, a policy of black and white lists can provide the best of both worlds.
Certificate - verify that HTTPS domains have a trusted certificate, ignore any certificate related errors (less secure) or block once certificate errors are found.
Rendering - define how the content is rendered. There are 3 options available:
- Frame - all browser content is transferred as frames (images). DOM elements, CCS, internal logic and API calls are hidden from the client.
- Stream - all media elements are streamed directly. Other elements are transferred as frames.
- Crystal - Some of the browser content is displayed as is - HTML elements such as DOM elements & CCS (which are considered safe). Other elements which are considered potentially harmful (internal logic & API calls) are hidden from the client. This is a Tech-Preview feature, available only when Tech-Preview features are enabled.
Block Ads - enable or disable ads on websites. Ads might consume resources and decrease performance so blocking them is highly recommended (enabled by default).
Note
Some sites might not function properly when ads are disabled. To solve this, first verify that it is indeed related to Block Ads. If this is the case, add a specific policy for each such site to enable ads in it (Block Ads = Disabled). End user can disable ads locally, while browsing, using the right-click-menu option Pause AdBlock & Reload. This will affect current session only.
System Defaults¶
The System Default policies are displayed in the first row of the table (in green). By default, all new domains are related to the All profile.
To change one of the defaults, click the specific option, and select the new value from the dropdown list. This will affect all domains/categories in the table that have the default value for this policy. Domains/Categories with pre-defined values will not be affected.
Override Values¶
Use the Override options (second line, in red) to define a specific policy value, effective immediately on ALL domains/categories. This is very useful on occasions when an overall change is required, due to security breaches, changes in company’s policies etc.
To apply an override, click the specific option, and select the desired value from the dropdown list. Once an override value has been set, the entire column is marked in red, to visually highlight that an override value has been set. The override value affects the entire system, not only the domains/categories defined in the table.
Override values take precedence over existing policies values and provides an efficient way to apply changes quickly thus improving overall protection in times where certain threats may be high.
To remove an override value and return the system to the previous settings, open the drop down values list and select the empty (last) option.
The override value is removed, and the previously set values are retrieved and displayed in the table.
View Profile Policies¶
Select the desired profile in the profiles filter to view this profile policies. The available options are according to the profiles defined in the system. Defaults and override values are kept per profile. For more information about defining profiles, go to Profiles. It is possible to define policies for a certain profile either by adding new policies or by modifying existing ones.
Policies Hierarchy¶
The more detailed, specific rule which exists in the system - takes precedence.
When the end user browses to a certain domain, these steps are carried out, to determine how to access this domain (and which policies will be referred to):
- First, the domain is looked up in the Policies table. If matched for a specific rule there - act according to the defined policies.
- Else, the domain’s category is looked up in the Policies table. If matched - act according to the defined category policies.
- Else, act according to the system default policies values.
Add New Policies¶
Add New Domains¶
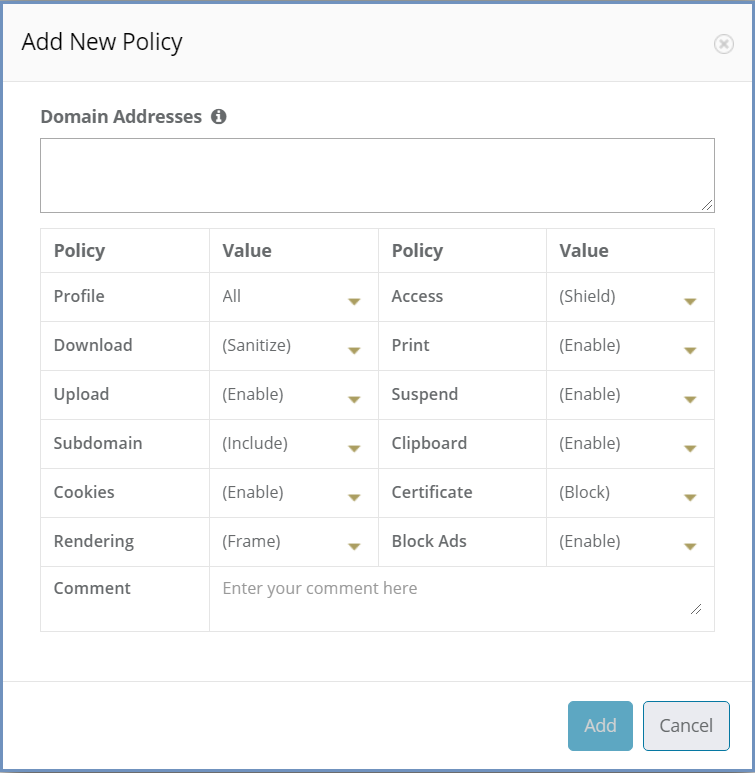
To add domains to the Policies table, press the Add New Policy icon.
The following dialog opens:
The dialog opens with the current system default options applied (per the selected profile).
Add the domains in the Domain Addresses field. Multiple addresses can be added, separated with a new line.
The domain can be, for example bbc.com, or www.bbc.com. Specific URLs (e.g. http://www.bbc.com/news/) are not supported, as the policies refers to an entire domain.
Define the required option(s) for this policy using the drop-down list of values. Once complete, click the Add button.
Note
IP addresses are also supported.
The added domains/IP address are validated to make sure there are no duplicates. This is to prevent the same domain/IP address having different options applied in multiple policies, which might lead to errors in connecting to that domain. Same domain/IP address may appear with different profiles. This is not considered a duplication.
If a duplication exists, a message is displayed stating the domain already exists (verified per a specific profile). The dialog remains open, allowing the user to modify the entered details.
Once the validation checks are successfully completed, the dialog closes and the new domains are displayed in the table. Each domain policies will take priority over the System Default policies, except if an override value has been set.
If a domain is marked as white in the Access policy, a notification is issued to the Administrator, confirming that only the specific domain is allowed, and any redirects from this site, will NOT be allowed unless they are also whitelisted. In addition, once the policy is displayed in the table, all settings that are irrelevant for a whitelisted domain are marked as crossed out text.
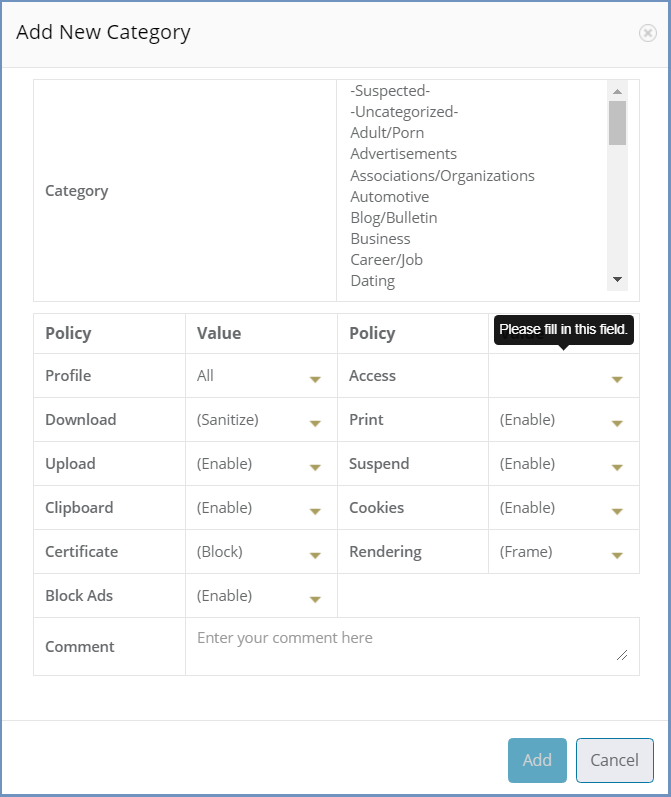
Add New Category¶
To add categories to the Policies table, press the Add New Category icon. This icon is enabled only with the matching license add-on.
The following dialog opens:
The dialog opens with the current policies default values applied (that match the selected profile).
Select the category from the drop-down list available in the Category Name field. Multi-select is available (using the CTRL/Shift keys), so multiple categories can be added at the same time.
Modify the different policies as desired (by using the drop-down list of values) or leave the defaults unchanged. Once complete, click the Add button.
The added categories are validated to make sure there are no duplicates. This is to prevent the same category having multiple definitions, which might lead to errors when a domain is identified to belong to that category. Same category may appear with different profiles. This is not considered a duplication.
If a duplication exists, a message is displayed stating the category already exists (verified per a specific profile). The dialog remains open, allowing the user to modify the entered details.
Once the validation checks are successfully completed, the dialog closes and the new categories are displayed in the table.
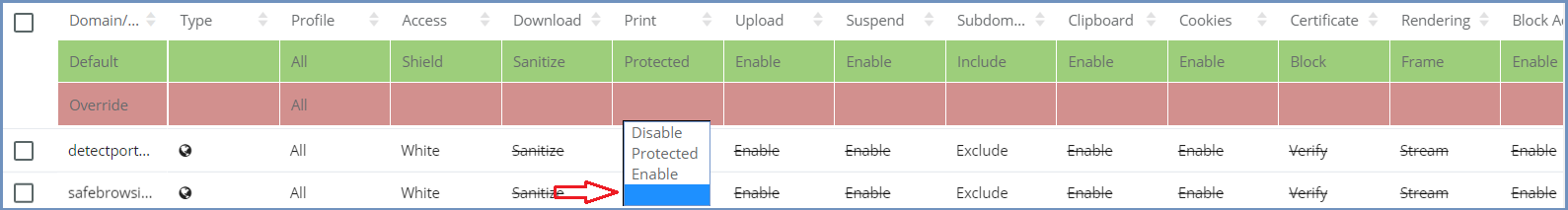
Update an Existing Policy¶
Once a policy is added to the table, it can be updated directly from the table itself. All columns are editable. To update a certain domain/category policy, click the entry to update (one click only) and the entire row become editable.
The Domain and comment columns are free text input fields and the other columns have drop-down lists of values to select from.
Once done updating the specific row – click outside the line (anywhere else on the table) and the updated values are validated (same checks are performed as when adding a new domain) and committed.
Note
Each update made in this section, once validated and committed, may take a few moments to apply. In addition, is relevant for new sessions only. These changes do not affect running sessions.
Pre-Defined Policies¶
Shield comes with a few pre-defined domains/IP addresses policies to begin with. In addition, if the Categories are enabled, they are included in the Policies table. These predefined policies are:
- detectportal.firefox.com - this site is used by Firefox when detecting whether it is using a captive portal. Since this site is commonly used and should work as expected in Shield - it is whitelisted by default.
- safebrowsing-cache.google.com - Safe Browsing is a service from Google that helps fighting the spam and phishing sites by blocking them in the browser. When shielded, this service causes unexpected behavior. Since this site is commonly used and very beneficial, it is whitelisted by default.
- IP address 169.254.169.254 - this IP is used in a few cloud computing platforms (e.g. Amazon EC2) to distribute metadata to cloud instances. In Shield It is blocked by default, to protect Shield metadata from outsiders reach.