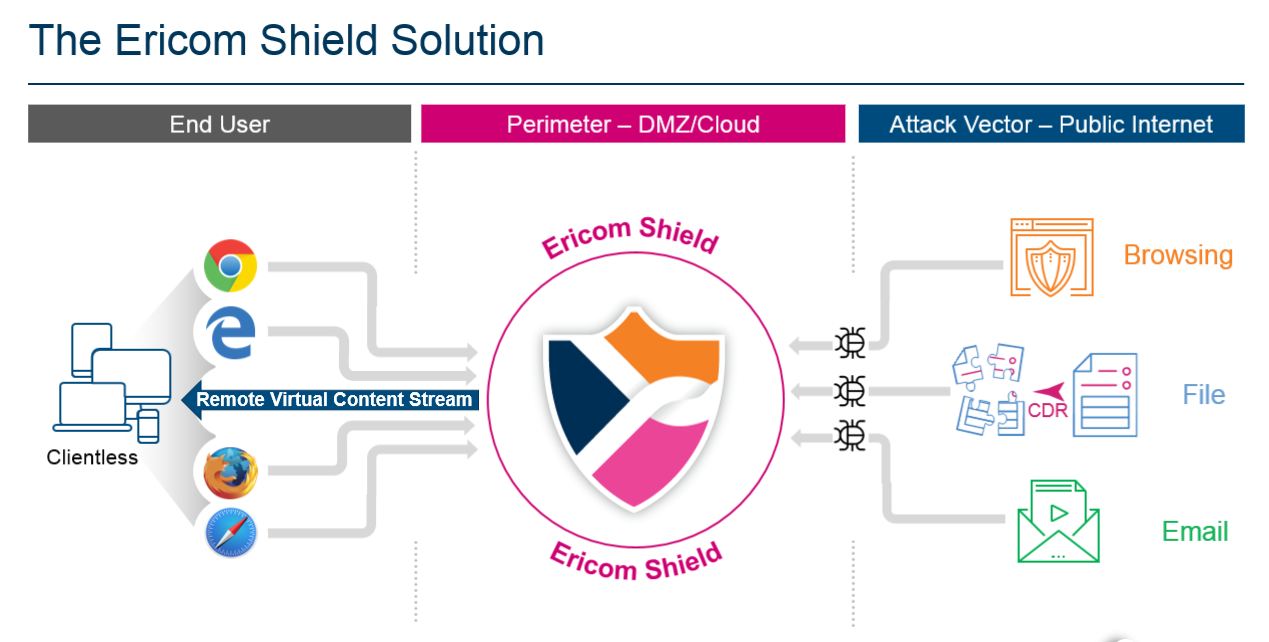
Ericom Shield Architecture¶
Ericom Shield is deployed as three separate logical components:
Shield Core
Ericom Shield Core includes:
- A standard Web Proxy designed to accept and direct all web requests. This is an optional component that can be replaced by any standard web proxy in use within the organization.
- An ICAP server that receives web requests from the proxy using the industry standard ICAP protocol and then processes the requests based on the defined business rules.
- A Policy Management Module that enforce policies on the web requests (White List/Black List/Clipboard/Download/Cookies etc.).
- The File Sanitization solution (CDR).
Shield Browser Farm
The Shield Browser Farm is a flexible virtual farm of micro Linux containers. Each container includes a secure browser and the Ericom rendering engine. The creation and destruction of these containers is managed by the orchestration component of the Shield Management.
Shield Management
The Shield Management includes the business logic database, orchestration components, logging and a web based Administrative console.
The above components are all installed as Docker containers on Ubuntu Linux servers.
Process Flow¶
A user navigates to a desired web page by entering a domain address in the browser address bar.
HTTP requests are sent to the proxy server (either enterprise or the embedded Shield proxy). The proxy server acts as an intermediate and delivers the desired web page to the user.
The proxy server is connected to the Ericom ICAP (Internet Content Adaptation Protocol) server in the Shield Core, which processes the given domain according to the predefined policies (white list, black list etc.) configured by the Administrator.
If the domain is blacklisted, then the connection is blocked and a message is displayed to the user. If the domain is whitelisted, it is opened directly, without going through Shield. If the domain is shielded, Shield Core allocates a Shield Browser from the available browser pool, a new dedicated container is assigned for the session and the desired domain is opened and delivered to the user.
The Shield Browser allows the user a seamless browsing experience, including all commonly used features such as video, audio, printing, downloading, according to the predefined policies configured by the Administrator.
When downloading a file, the downloaded file is first sent to the Content Disarm and Reconstruct (CDR) engine, which is designed to deconstruct the file and remove any content that can cause potential harm (both known and unknown threats). Once the file sanitization is complete, the sanitized file is sent to the user.
When the session ends, and the user closes the browser, the container is destroyed and a new container is created.