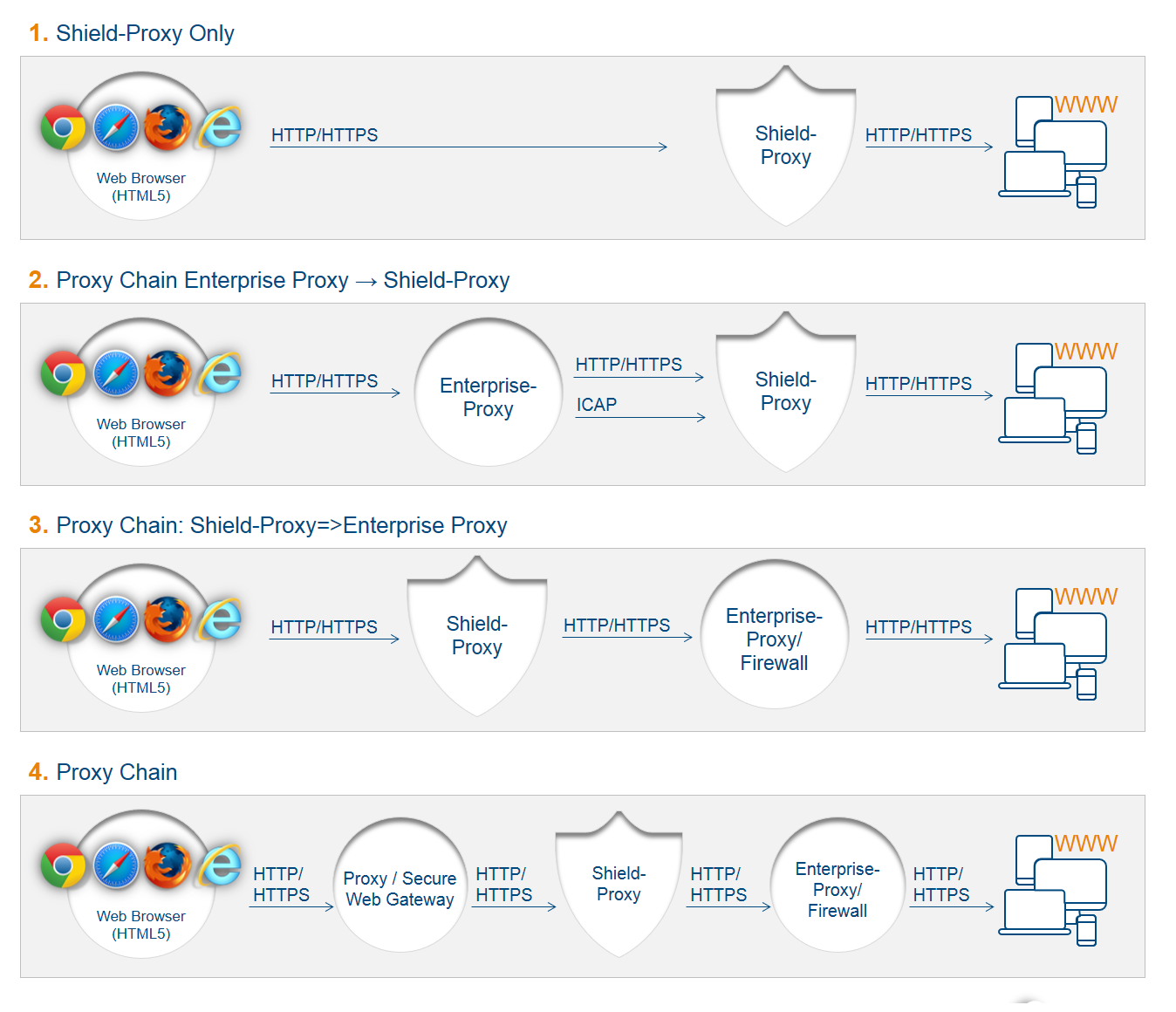
Deployment Topology¶
There are several possible topologies for Ericom Shield in an existing customer’s environment.
In the existing environment, there may be several components within the connectivity chain, between the end-user and the internet. Ericom Shield needs to be integrated into this connectivity chain. There might be one or more existing proxies, or none at all. There might be a firewall or multiple firewalls and a DMZ. Shield can be placed in various positions along this chain.
The recommendation is that Ericom Shield Core and Browsers Farm components be placed in the DMZ, as this is the safest and most secure deployment. The Management component should be in the Domain. However, the customer’s existing environment will determine the final topology, taking in account all parameters and components, to ensure optimal deployment for Ericom Shield.
Here are a few example topologies: